试题内容
网络管理员在安全防护系统看到如下日志,说明该信息系统受到()攻击。
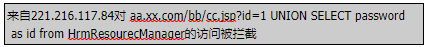
A.SQL注入
B.DDoS
C.XSS
D.HTTP头
查看答案

A.SQL注入
B.DDoS
C.XSS
D.HTTP头
软题库参考答案:A(仅供参考)
软题库解析:正在加载....

你可能感兴趣的试题
All three types of cryptography schemes have unique function mapping to specific.For example, the synunetric key(71) approach is typically used for theencryption of data providmg(72), whereas asymmetric key cryptography is maidy used in key(73)and noruepudiation, thereby providing confidentiality and authentication. The hash(74)(noncryptic), on the other hand, does not provide confidentiality but provides messageintegrity, and cryptographic hash algorithms provide message(75)and identity of
第15题:电信运营商提供的ISDN服务有两种不同的接口,其中供小型企业和家庭使用的基本速率接口(BRI)可提供的最大数据速率为(1),供大型企业使用的主速率接口(PRI)可提供的最大数据速率为(2)。 Linux系统中,DHCP服务的主配制文件是(1),保存客户端租约信息的文件是(2)。
(1)A.dhcpd.leases
B.dhcpd.conf
C.xinetd.conf
D.lease.conf
(2)A.dhcpd.leases
B.dhcpd.conf
C.xinetd.conf
D.lease.conf